A Secure Erasure Code-Based Cloud Storage System with Secure Data Forwarding





Mentors :
Khushang Singla
Nilabha Saha
Mentees :
4-5
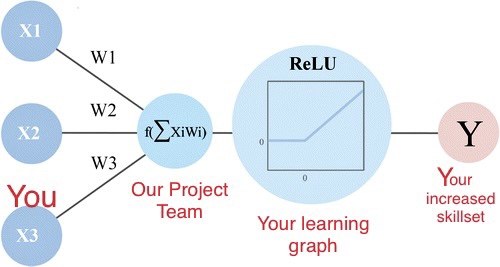
In this project, we will create a secure and robust distributed storage system that can be employed on the cloud. We shall ensure robustness in the sense that even if a few servers fail, there is sufficient redundancy in the data stored to successfully retrieve the data, while also ensuring that said redundancy does not occupy excessive space. We shall ensure so using a decentralised encoding scheme. Furthermore, we shall ensure that the data is kept confidential by suitable cryptographic mechanisms. We offload the hassle of key management from the users to the cloud keyservers in such a way to ensure that even the full compromise or failure of a few keyservers does not leak the encryption keys to a malicious adversary. Moreover, we also implement a proxy re-encryption scheme which allows the cloud servers, upon and only after taking permission from a user, to re-encrypt their data into an encryption of a different user's data in such a way that the cloud servers learn no information about the underlying data throughout the process.
Our system would be developed in a way so as to put little computational load on the users and little communication overhead between the users and the cloud.
We will be implementing the following paper: https://ieeexplore.ieee.org/document/6035700
We would use Docker to simulate the cloud environment and use socket programming in Python to enable communication between the systems. We would also use SageMath for implementing the cryptographic mechanisms required.
*Note:* This would be a full-fledged project which could be expected to be deployed on real systems with minor modifications. We expect around 6 hours of work per week on average for successful completion of the project.
Prerequisites (Desired but not necessary):
Python is a must. You should have interest in cybersecurity.
Tentative Timeline :
| Week | Work |
|---|---|
| Week 1-3 | Socket programming with multiple simultaneous clients, Docker for simulating cloud environment, Sphinx Documentation |
| Week 4 | Complete Paper-Reading |
| Week 5 | Implement pairings over elliptic curves and the System Setup |
| Week 6-7.5 | Set up database, Implement Data Storage, Data Forwarding, and Data Retrieval |
| Week 7.5 - 8 | Final touches |